What does that Fitbit, that you are wearing on your wrist to track your steps, have in common with smartphones, automobiles, medical devices, anti-theft devices, and drones? Give up?…. micro electro-mechanical systems (MEMS) accelerometers. These little devices are being used in cell phones for step counters, user interface control, switching between portrait and landscape mode, and the built-in camera. They are also used in camcorders for image stabilization and have been used in computer hard drives to detect a laptop freefall and switch the hard drive off to prevent damage. They are used in cars to detect a car crash to deploy airbags and are used in military and aerospace systems, such as in airplanes for navigation. The number of devices that use MEMS accelerometers are countless.
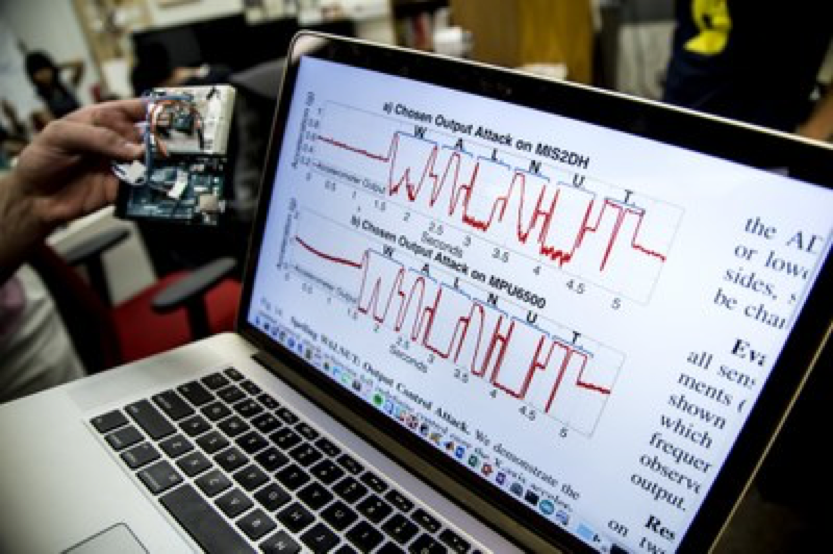
Now you would think that these devices would be protected from being hacked, right? Well… not so much. A team of researchers at the University of Michigan and University of South Carolina tested the effect of sound waves on 20 different MEMS accelerometers from 5 manufacturers. In one test they tricked a smartphone’s MEMS accelerometer, by playing a YouTube music video laced with special tones, to output a signal resembling the alphanumeric string “WALNUT”. Then they did other alarming things as well. But before I get into that, some of you might be wondering:
What is a MEMS accelerometer?
MEMS accelerometers are electromechanical devices that measure acceleration forces, that is, they measure changes in velocity and position. It has become a field, in which mechanical elements, like cantilevers or membranes, have been manufactured at the scale of a microelectronics circuit. While electronic circuits are solid and have compact structures, MEMS have holes, cavities, channels, cantilevers, and membranes, and in some way, imitate mechanical parts that are less than 100 micrometers in size. The 2008 paper by Matej Andrejasic gives a great description of MEMS accelerometers and how they are made.
The first MEMS accelerometers were designed in 1979 at Stanford University, but didn’t really get much use until the 1990’s when they revolutionized the automotive airbag industry. Then the industry exploded and other types of MEMS sensors were being developed to be used for different applications, such as pressure sensors, bioMEMS, Optical MEMS (MOEMS), RF MEMS, and others.
So, whether we are aware of it or not, they’re in our devices that we use on a daily basis. Take your car, for instance. It has at least 50 MEMS. They are used in its safety systems such as airbags, electronic stability control and tire pressure monitoring systems. That cell phone that you have with you all the time has at least 14 MEMS sensors. In commercial and the military, they are used in satellites, drones, and aircraft systems. In the medical field, they are used for monitoring blood pressure and many other areas. In gaming systems, they are used in the Xbox and (if you still have it) the Wii. To see many of the applications MEMS are used in, this site by MEMS & Nanotechnology Exchange gives quite a list.
How does the attack work?
For the vulnerability we are discussing, it lies with the MEMS inertial sensors (or MEMS accelerometers). Now, what the team of researchers did was to see what would happen if they delivered high intensity acoustic interference in close proximity to a target MEMS sensor and attempted to fool the sensor into outputting arbitrary signals. (If you want all the details of the attack, there is a whole paper and videos to show what was done at the University of Michigan’s site).
In their first test, they got the MEMS to output “WALNUT”, but on other tests they injected steps into a simple fitness monitor from Fitbit. On another attack, they piloted a car, well not a real car, but an RC car. They ran the acoustic attack onto a Samsung Galaxy S5 running an application to pilot the RC car.
Why should we be concerned?
You might be wondering why should I be concerned about adding steps to my Fitbit or controlling a toy car? The problem is that the same kinds of MEMS accelerometers are used in real cars, drones, airplanes, medical devices, autonomous vehicles and other devices. Now the attack does require some sophistication and would need to have specific information on the sensor data and the signal an attacker would be trying to spoof. But, with the increased use in medical devices and the growth of autonomous vehicles, an attack against all MEMS, not just MEMS accelerometers, should be treated seriously. What’s the future possibility of a laced music video, automatically played from a website, email attachment, Twitter link tapped on a smartphone, etc., be used to take control of an autonomous vehicle? The potential for misuse in a social engineering context is similar to other instances in which technology has been used to either trick someone into an unsafe action or to take control of a resource. We need to mitigate all attack vectors now, because our lives will depend on it.
What can be done?
Unfortunately, there isn’t anything we can do at the moment but be aware and to practice good anti-social engineering habits such as not clicking on unknown files from unverified senders. But there is something that the manufacturers can do. As responsible researchers, the University team has notified the manufacturers on the issues and ways they can adjust the hardware design to fix the problem, for example, designing them to better tolerate acoustic interference with a Secure Low Pass Filter. They also recommended some low-cost software defenses that could minimize the vulnerabilities. You can read about these fixes in their report. Hopefully, the manufacturers listen. Otherwise attacks will happen with devastating consequences.
Sources:
http://mafija.fmf.uni-lj.si/seminar/files/2007_2008/MEMS_accelerometers-koncna.pdf
https://www.usenix.org/system/files/conference/usenixsecurity15/sec15-paper-son-updated.pdf
https://www.usenix.org/system/files/conference/woot16/woot16-paper-davidson.pdf
http://www.dtic.mil/dtic/tr/fulltext/u2/a282470.pdf
http://www.dtic.mil/dtic/tr/fulltext/u2/a428707.pdf
https://gizmodo.com/hackers-can-now-use-sound-waves-to-take-control-of-your-1793259066
https://spqr.eecs.umich.edu/emi/
https://spqr.eecs.umich.edu/papers/trippel-IEEE-oaklawn-walnut-2017.pdf
https://spqr.eecs.umich.edu/walnut/#faq-practical
https://www.mems-exchange.org/MEMS/applications.html
http://www.pcmag.com/encyclopedia/term/37372/accelerometer
http://www.engin.umich.edu/college/about/news/stories/2017/march/sonic-cyber-attack-shows-security-holes-in-ubiquitous-sensors
http://internetofthingsagenda.techtarget.com/definition/micro-electromechanical-systems-MEMS https://blog.adtile.me/2015/11/12/were-you-aware-of-all-these-sensors-in-your-smartphone/ http://www.darkreading.com/sound-waves-used-to-hack-common-data-sensors/d/d-id/1328422
1 Comment
Comments are closed.


though cellphones can be controlled from that of the sound waves, but if a high magnitude of sound waves is not inputted, then it will result in 0 for controlling the cars, I do think a step towards the theoretic explanation is a step forward.