At Social-Engineer, LLC (SECOM), we define social engineering as “any act that influences a person to take an action that may or may not be in their best interest.” If you Google “social engineering,” you will get a very different and more negative definition. However, I prefer our definition, with more broad and general terms, because I feel that social engineering is not always negative. Rather, it encompasses how we communicate with our parents, therapists, children, spouses, and others. No matter how you define social engineering, it can be used for good or bad, just like anything else. Because of this, we need to dive into it more deeply to truly understand what it is and how it can be leveraged. By understanding social engineering from the attacker perspective, you’ll be in a better position to protect yourself.
Breaking it Down
There are two major keys to whether a social engineering attack is successful or not that we are going to dive into today:
-
- The attacker perspective, and
- Education and security culture at your company.
Attacker Perspective
You may have noticed that “Attacker Perspective” is a keyword in this newsletter’s title. Why is that and what makes it so important? Let’s define it before we discuss. “Attacker Perspective” is defined as “a view of the world where every piece of information can be used for personal gain or leveraged to achieve a desired goal.” When I think of Attacker Perspective I think of these guys:

If you’ve seen the Oceans’ movies you know what this team does. They are able to find a target, set their goal, and make a plan to get it done. They have the ability to look at a building, see its vulnerabilities, and determine the various ways to attack it. This same perspective is used in social engineering attacks. For the purpose of our discussion today, let’s use vishing as an example.
What is Vishing
Vishing is defined as the “practice of eliciting information or attempting to influence action via the telephone.” I can almost guarantee that you have received one form of a vishing call or another. For example, when was the last time the kind people at the IRS informed you that your social security number was stolen? Not only that, but they’ve decided that the best way for you to get it back is to pay them for it!
Or how about one like this; here is a transcript of a call I received: “Before we close the file, if you were interested in renewing your auto warranty now, please press 5 now or press 9 to be removed from our list.” Sound familiar? So, there we have 2 common vishing scams at their most basic.
Attacker Perspective Lens Applied to Vishing
How can we fit the attacker perspective lens to vishing? With this attack vector, rather than targeting a physical building, the target is the individual. The goal is the information you can obtain while talking to the target on the phone. Sophisticated attackers can look at the information available about you or your company and understand how to best leverage it against you.
Is it Successful?
You might be wondering, though, if these attacks are truly successful. Well, in 2021 alone, TrueCaller reports that Americans lost $29.8 billion to phone scams. Cleary, this is a prevalent attack vector.
Why Does it Work?
Now, it’s true that not all of this money was lost due to simple IRS scams. You’re probably even thinking that there’s no way you would fall for one! However, we are, all of us, susceptible to social engineering attacks given the right combination of environmental and emotional triggers. I’m going to repeat that again for the skeptics; we are ALL susceptible to social engineering attacks given the right combination of environmental and emotional triggers.
Understand SE Tactics and Emotional Triggers
How? How are we all susceptible? We are all human. Most of us experience the same base emotions, no matter how much they may vary from person to person. For example, fear, greed, and curiosity are 3 emotions that attackers leverage. Even the simple IRS scam we discussed previously used all of these.
Now, again, that doesn’t mean we would all fall for the IRS scam. But think about those emotions and tactics when leveraged in the hands of a sophisticated attacker. An attacker that knows how to use these emotions to their advantage and has honed their attacker perspective can be extremely dangerous.
What Does This Mean for Us?
If you can continue to learn this perspective and see how attackers think, you will be in a much better position to protect yourself when it may be necessary. That’s what we specialize in at SECOM; understanding this perspective in order to find these vulnerabilities and then training your employees how to guard against them.
So, how can we protect ourselves, our families, and our companies? Start by being aware of what information is available about you. Then, start practicing your own attacker perspective. How? Remember, the first thing the Oceans team does is look at their target. Imagine yourself as the target. Then, examine the ways you might attack yourself. For example, do you post on a public social media account all about your love for CrossFit? A CrossFit-themed vishing call may be just the handhold a real attacker needs. Now you’re aware of at least one potential vulnerability!
Many people in the information security industry have different approaches to reducing your potential attack surface. With things like CrossFit, for example, I’m in the party of “be aware and alert.” Once you’re aware of what you display about yourself, you can be alert. If someone direct messages you trying to build rapport using CrossFit, then works their way into asking more personal questions… that could be a red flag! Practicing this perspective will in turn allow you to stay more secure.
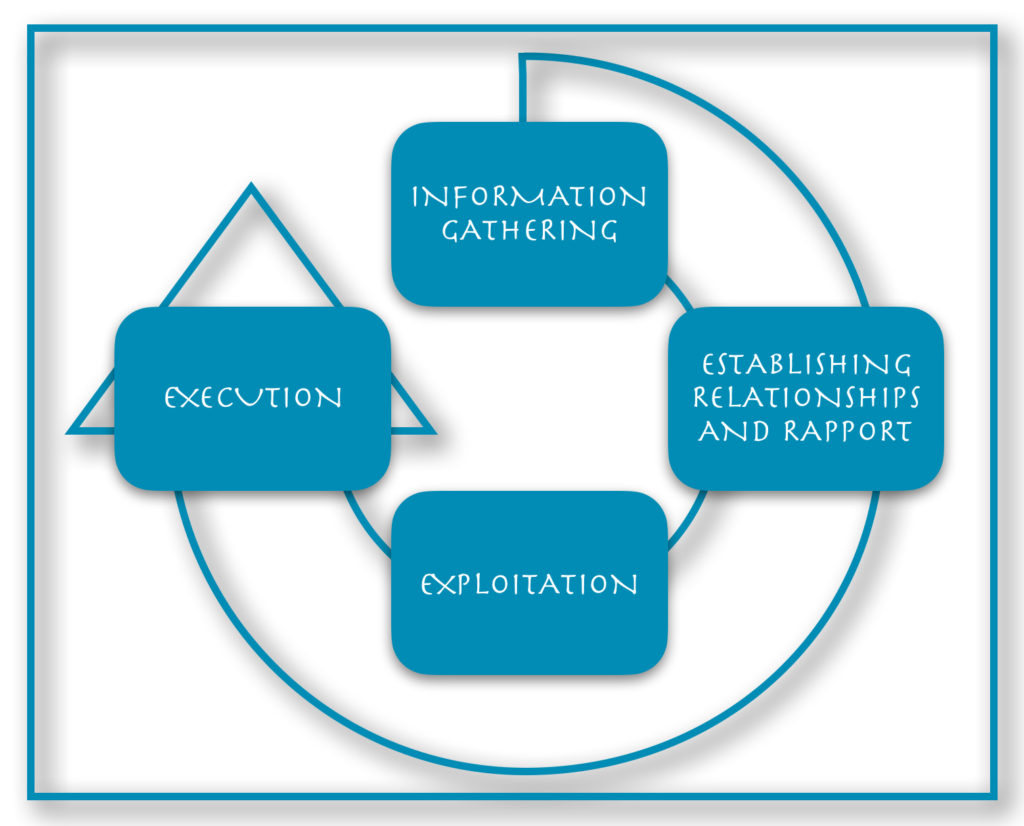 Education is Key
Education is Key
We have taken some time today to look into the attacker perspective and educate ourselves on how to be safe from those who would use it maliciously. However, many haven’t taken this step yet. That is why education surrounding information security is SO important. I encourage you to explore the links I’ve placed throughout this article. They go in-depth on topics that we didn’t have enough time to delve into today. Continue your own education and share the resources with your family and coworkers. This is the only way we can grow and learn as a society and protect ourselves.
Written by: Shelby Dacko
Sources:
https://www.imdb.com/title/tt0240772/
https://www.social-engineer.org/framework/attack-vectors/how-can-you-protect-yourself-against-common-attacks/
https://www.social-engineer.org/framework/attack-vectors/phishing-attacks-2/
https://www.social-engineer.org/framework/attack-vectors/impersonation/
https://www.social-engineer.org/framework/attack-vectors/smishing/
https://www.social-engineer.org/framework/attack-vectors/vishing/
https://www.social-engineer.org/framework/attack-vectors/attack-cycle/
https://www.imdb.com/title/tt0240772/mediaviewer/rm3294408704/
https://www.social-engineer.org/framework/general-discussion/social-engineering-defined/
https://www.social-engineer.com/glossary/vishing/
https://truecaller.blog/2021/06/28/us-spam-scam-report-21/
https://www.social-engineer.com/
https://www.social-engineer.com/training-courses/

