Ransomware and The Psychology Behind Why It Works

May 12th, 2017, ransomware really got put on the map, with WannaCry (WanaCrypt0r 2.0) encrypting over 200,000 systems in 150 countries. The demand: $300 (US) worth of Bitcoin to decrypt your data. Who was hit: 61 National Health Service organizations in the UK, Nissan, FedEx, telecom and gas companies in Spain, some Renault factories in France, the interior ministry in Russia, Germany’s rail network, and the list goes on.
How did this happen and why does this form of attack work so well?
Ransomware isn’t new. It first appeared way back in 1989, as PC Cyborg (AIDS) Trojan. (It wasn’t a money maker but it does go down in the history books.) Throughout the years, ransomware has appeared in various forms, such as Cerber, CryptoLocker, Locky, TeslaCrypt, TorrentLocker and many others. All had the same goal; find a way to infiltrate the system, lockup the system or encrypt all the files and demand payment to unlock the system or decrypt the files.
Because of the growth of the Internet and the ease of transferring funds, especially with the hard (sometimes impossible) to trace cryptocurrency, and the quick and easy return on investment, this form of malware is becoming more popular. This has become a $1 billion dollar industry, according to CSO. Then you combine them with the use of exploits (many now provided by the NSA leak) and you have the perfect weapon to use against unsuspecting users. That is what happened with WannaCry; it used the EternalBlue exploit that was used against MS17-010, a vulnerability in the MS SMB protocol. It then propagated on its own to other systems in the same network that had this vulnerability.
How does ransomware get into the system in the first place?
Let The Mind Games Begin
Simple – the target gets a specially crafted email, like a spear-phish or a targeted email for their particular job category. They click on a link that directs them to a specially crafted site that automatically downloads the malware or they open a document in the email and it installs from there. Another means can be by clicking on an infected advertisement or visiting an infected website.
As an example, back in January, I received a phone call from a friend. She was in a panic; she said she opened an email that had an invoice attached, she clicked to open it and then this message popped up:
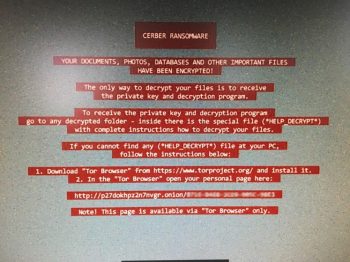
What made her decide to click on the attachment? At the time, she was working on invoices for the company she works for and not noticing that it wasn’t someone she usually gets invoices from, she clicked to open it.
This brings us to why ransomware works so well. Troy Hunt says it well, “Attackers are really figuring out how to tap into not just the digital side of things to compromise systems, but how to tap into people’s psyches and push the right buttons that will cause them to pay.”
What are those buttons? Here are some of the mind tricks they use to be successful:
It starts with the email; the potential victim receives an email addressed to them. It’s personalized, the wording and message is something that they would normally see. Since it looks legitimate they click on the link or attachment, like an invoice or fax, and open it. What the attacker is doing is to quickly build trust and to override the target’s ability to critically think and to make them react based on emotion (how often do we make good decisions based on emotion???).
This is what happened to my friend. She was very busy with work, processing invoices, an email comes in that looks legitimate and has an invoice attached to it. So, she opens it without thinking.
Another example of how attackers are doing this involved the spread of the ransomware called Philadelphia that affected health organizations. According to Healthcare IT News, employees received a spear-phishing email. Instead of a traditional attached file, users were directed to a link found in the email. Once clicked, the site redirected and downloaded a malicious Microsoft Word file. The document contained the logo of the targeted healthcare organization and a signature from a medical practitioner from that organization. In addition, the file contained icons resembling patient information. All this made the whole pretext look legitimate and compromised the victims’ critical thinking.
Another trick to watch out for are websites we visit. According to the site FBI.gov/news, FBI Cyber Division Assistant Director James Trainor is quoted, “These criminals have evolved over time and now bypass the need for an individual to click on a link. They do this by seeding legitimate websites with malicious code, taking advantage of unpatched software on end-user computers.” So, watch out for compromised adds or websites.
After the ransomware takes over, the mind games continue.
You know those sales adds where they say the sale will only last for one day and if you don’t act now you will lose out? Well, the attackers use the same ploy, to instill a sense of urgency and cause you to bypass all critical and rational thinking and to react with your emotions. They display a clock or timer ticking away, with the threat that if the ransom is not paid in a certain amount of time, some files will get deleted or the price is going up.
Another button they press is the threat of public disclosure. They use this to instill fear that information that was captured will be released if they don’t receive payment. This threat of using defamation and extortion is very effective, especially to healthcare organizations with the possible disclosure of sensitive patient information, such as PII and medical records.
How can organizations and individuals keep from falling prey to the mind games that the attackers are using?
Minimize The Risk
The following 4 points should help:
1. Training and Education:
Businesses should train their employees how to recognize phishing emails and inform them of the critical role they play in protecting their organizations data. Don’t just take my word for it. N’Gai Oliveras, IT director at the Office of the Comptroller of Puerto Rico, is quoted in the TechRepublic article where he recommends increasing training for end users as one solution. He says, “In these times, we in senior management need to be more focused on providing more security awareness trainings to our users, instead of looking for more ways to strengthen our networks,” he said. “In my opinion, our users are the most effective line of defense in our networks.” In the same article Chuck Elliott, VP and CIO of Concord University said, “We should all be highly motivated to continue minimizing threats and intrusions, and increase our efforts to educate users of our networks.” So, IT professionals are agreeing that education is one of the main keys to combat the mind games and keep ransomware from getting into the network.
2. Policies:
Organizations need to implement software restriction policies that help prevent malware from running. A computer use policy is also needed; don’t give users admin privileges. Configure access controls, including file, directory, and network share permissions appropriately. If users only need read rights to specific information, then don’t give them write-access to those files or directories.
3. Protection:
In addition to endpoint and server based A/V scanners, organizations need to implement runtime malware defenses to stop the ransomware that gets past antivirus. Identify vulnerable systems using scanning tools like Nessus, and patch these vulnerable systems and upgrade any deprecated OS as soon as possible. Only have ports open you absolutely need and perform a regular audit of them. Implement an email gateway with machine-learning function and real-time IP reputation scanning. For the best results, look for a security solution with email attachment scanning, performed in the cloud via static and dynamic (sandbox) malware analysis, so email attachments are checked for bad behavior before they’re delivered, and not just known bad reputation or known signatures which tend to miss zero-day attacks. For those unaware, make sure Macros are disabled for documents.
4. Business Continuity Plan:
All need to have a proper backup and recovery strategy in place and test it regularly. The 3-2-1 approach works well if your organization can do it. For those unfamiliar with it, it’s having 3 copies in 2 different formats and one copy stored offsite. Secure your backups. Make sure they aren’t connected to the computers and networks they are backing up. (Test your backups and make sure they are good, you don’t want to be in recovery mode and your back up is no good.)
What if you already got compromised, should you pay? What do you do?
Do I Really Want To Be a Cash Cow?
If you think you or your organization have been the victim of ransomware you can report it:
- US: contact your local FBI field office and report the incident to the Bureau’s Internet Crime Complaint Center or you can report it here https://www.ic3.gov/default.aspx.
- UK: you can report here: http://www.actionfraud.police.uk/report-a-fraud-including-online-crime-questions.
- Other parts of Europe you can report it here: https://www.nomoreransom.org/,
- Australia: you can report it here: https://www.scamwatch.gov.au/report-a-scam.
Should you pay the ransom? According to the message from the UK’s National Crime Agency they say, “do not pay! – there is no guarantee that systems will be restored.”
The only thing left to do is restore what you can from backup and learn from what happened.
So, if you have been infected or not, learn to not fall for the mind games that attackers use. Learn from these events and follow the 4 points mentioned to make your environment more secure. Educate and train yourself and fellow employees to recognize phishing emails, implement policies that will secure the network, protect the network with a layered approach and have a proper business continuity plan in place and regularly tested. Doing this will not be a 100% guarantee that the network won’t be compromised but it sure will reduce the risk, and that’s what matters.
Stay safe.
Written By: Mike Hadnagy
Resources:
https://www.welivesecurity.com/2015/09/18/evolution-ransomware-pc-cyborg-service-sale/
http://money.cnn.com/2017/05/15/technology/ransomware-wannacry-explainer/ https://www.datto.com/blog/common-types-of-ransomware
https://www.ft.com/content/af74e3f4-373d-11e7-99bd-13beb0903fa3 https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/why-ransomware-works-psychology-and-methods-to-distribute-infect-and-extort http://www.securityfocus.com/advisories/700
http://www.csoonline.com/article/3154714/security/ransomware-took-in-1-billion-in-2016-improved-defenses-may-not-be-enough-to-stem-the-tide.html
http://www.healthcareitnews.com/news/new-ransomware-spotted-targeting-healthcare-industry
https://www.fbi.gov/news/stories/incidents-of-ransomware-on-the-rise
https://www.techrepublic.com/article/cybersecurity-two-thirds-of-cios-say-threats-increasing-cite-growth-of-ransomware/

