The Onion, the Internet’s favorite parody news site, was recently the victim of a hack that compromised their corporate Google Accounts as well as their Twitter accounts. They were hacked by the Syrian Electronic Army (SEA). [You may have heard of the SEA.] They’re the group that hacked into the AP Twitter account and announced that two bombs went off in the White House injuring President Obama. This news sent the DOW plummeting; erasing billions of dollars from the exchanges. [Yeah, those guys.] Using the same method, phishing, the SEA orchestrated a three-staged social engineering attack that yielded access to the The Onion staff Google accounts and Twitter accounts. Let’s take a look at how they did it.
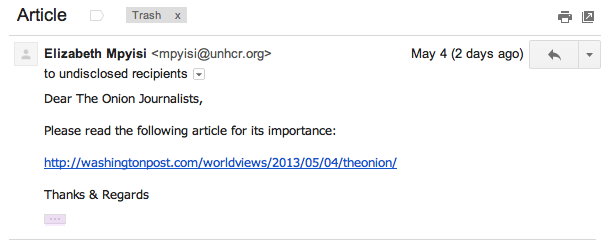
Step one: SEA sent out a limited-audience phishing email targeted at the reporters and writers. The email looked like an email from the Washington Post encouraging the recipients to review the linked article.
Instead of linking to a legitimate Washington Post article, the link presented users with a prompt to enter their Google Account credentials. Because this email was sent from an unknown outside address, not a lot of people clicked on it (let alone enter their credentials), but one did. That’s all it takes.
Step two: Using the Gmail account of the person who entered their credentials, the hackers sent the same email out to different members of The Onion staff. Because this email came from a presumed trusted source, an Onion employee, it had a much higher success rate. One of the users who entered credentials had access to all the company’s social media accounts. Now the hackers had access to all The Onion’s social media.
The Onion IT sent out important emails requiring everyone to reset their passwords. What The Onion staff didn’t realize is the hackers had access to another, previously unknown account and were monitoring things.
Step three: When the hackers saw the password reset email go out, they immediately sent another phishing email, to all staff except IT, with a password reset link! This duplicate message compromised even more accounts and the SEA began posting editorials under The Onion’s Twitter account. The final step was a forced reset of every Onion employee account.
Consistent, real world education is the only way to protect your organization from the threats of social engineering. Once again we see another high profile hack, perpetrated by sophisticated hackers, utilizing the tried and true methods of social engineering… a relatively low-tech approach.
6 Comments
Comments are closed.


Maybe I expect too much but a good spam filter should have intercept the first phishing emails. If nothing else, the tampered link must have been alerting even for a simple filter.
@Peter,
Rather than relying on a technological barrier to stop the spam, you could attempt to educate the people about net sec.
Just a thought.
Thanks for a marvelous posting! I truly enjoyed reading it, you might
be a great author.I will always bookmark your blog and will
come back from now on. I want to encourage you to continue your great job, have a nice weekend!
Please let me know if you’re looking for a article writer for your site.
You have some really good posts and I feel I would be a good asset.
If you ever want to take some of the load off, I’d love to
write some content for your blog in exchange for a link back to mine.
Please blast me an email if interested. Kudos!
Other than this it is effectively used for CRM, content management and more.
It is for this reason that more and more companies are getting into the ROR development and eager to hire the ROR programmer.
Here are few points to ascertain before hiring a Java Developer:
.
This real life example of Phishing by sophisticated hackers is astonishing and an eye opener. While education is the way to protect the organisation from the social engineering threat, here are additional ways to avoide phishing scams:
1) Think before you click- Don’t click on random mails. Check the source of the mail and thoroughly scrutinize the mail before clicking on any links.
2) Install an Anti-Phishing Toolbar- These toolbars run quick checks on the sites and compare them to lists of known phishing sites.
3) Verify a Site’s Security – Whenever you visit a website, always make sure the site’s URL begins with “https” and there should be a closed lock icon near the address bar.