Phishing
“In the field of computer security, phishing is the criminally fraudulent process of attempting to acquire sensitive information such as usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication” [1].
Protection from Fraudlent Messages
We typically associate phishing emails with poor grammar and misspellings. However, this is not the case in modern phishing, as they are now very realistic replicas. The best defense against fraudulent messages is to not click on the embedded links. Or, to use the log in fields embedded within the messages themselves. Instead, manually type in the trusted entities address into your browser. It’s important not to copy it from the message, or use a previously saved bookmark.[2]
URL and Email Manipulation
One reason why phishing schemes work so well is that people tend to trust messages that appear to come from an important entity or look important. Indeed, the attacker can easily manipulate a URL to look authentic fooling the victim to click on it. For instance, a URL such as (http://www.company.com) looks almost identical to (http://www.cornpany.com) if the font is right and the reader scans over it. Indeed, an attacker can purchase a domain that closely resembles the legitimate URL. Then, the attacker sets up an email account and spoofs the website. This requires very little time and effort. This seemingly simple process fools many people into clicking the link and then being hacked.
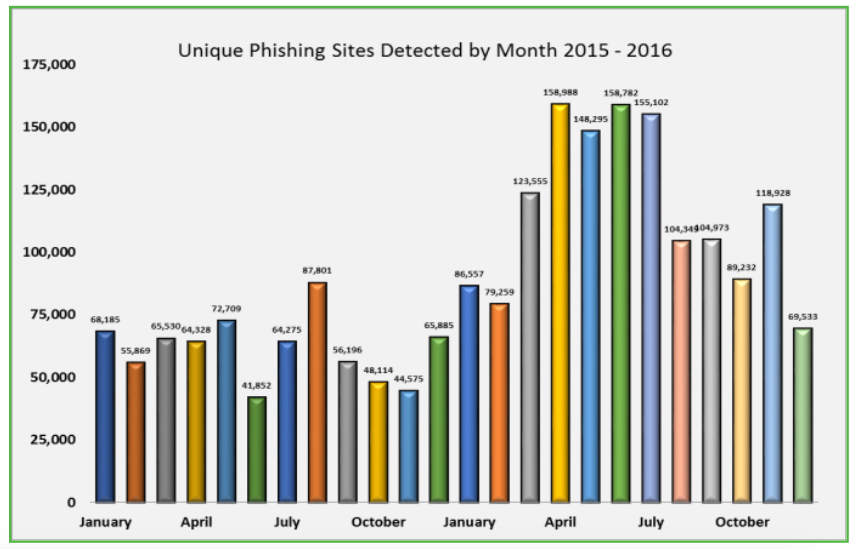 Phishing Attack Campaigns in 2016 Shatter All Previous Years’ Records – APWG
Phishing Attack Campaigns in 2016 Shatter All Previous Years’ Records – APWG
Spear Phishing
Due to the success of phishing attacks, malicious phishers have developed spear phishing. Instead of sending out thousands of e-mails randomly hoping a few victims will bite, spear phishers target select groups of people who have something in common and who usually have higher profiles. The emails are usually sent from organizations or individuals the potential victims would normally get emails from, making them even more deceptive.
 Cloudmark Survey 2016
Cloudmark Survey 2016
Penetration Testers
Penetration testers employ the same methods as criminals in order to show a company how devastating these attacks can be. Many companies will spend thousands of dollars on IDS systems, firewalls and other protection devices to monitor the network, but one fraudulent email can lead to total devastation in a company without having to hack one thing.

