SMiShing
At Social-Engineer, we define SMiShing as “the act of using mobile phone text messages, SMS (Short Message Service), to lure victims into immediate action. This action may include downloading mobile malware, visiting a malicious website, or calling a fraudulent phone number.”
The word SMiShing comes from combining SMS, the technology behind texting with phishing, the practice of stealing personal or financial information through deceptive emails. Basically, SMiShing is phishing but by another means, namely text messages on mobile devices. SMiShing texts are malicious social engineering scams that aim to influence people into turning over sensitive data such as:
-
- Social Security numbers,
- Credit card numbers,
- Account passwords, or
- Access to a company’s computer system.
To achieve this goal, criminals craft convincing SMiShing texts to make the receiver think the communication is from a familiar or trusted source. The bad actor may influence the target’s emotions by using social engineering tactics. The SMiShing text may sound urgent. For example, it may say that immediate action must be taken to secure a benefit or prize, or to resolve a problem.
NOTICE: Never use this information to perform illegal acts! The purpose of the Social Engineering Framework is to help ethical social engineers learn the skills they need in their adversarial simulation jobs. We also discuss these details to educate organizations about possible social engineering attacks. This can also help organizations decide which services may help them defend against these attacks.

Image: https://unsplash.com/photos/mz1rMariQ7w
SMiShing a Serious Threat
SMiShing attacks are a serious threat that can lead to a compromise of both personal and corporate information. For instance, many employees now access corporate information and accounts from their personal phones. If an employee falls victim to SMiShing on their personal phone, the attacker could get access to corporate information.
Since many SMiShing texts have links to phishing websites, it is challenging to find specific statistics just for SMiShing attacks. However, they are on the increase. The 2020 FBI Internet Crime Complaint Center reports that companies lost an alarming $54,241,075 as a result of social attacks including SMiShing, vishing, and phishing. Several factors are, no doubt, contributing to the rise in SMiShing. First is the widespread use of smartphones. It’s reported by Statista that there are over 6 billion active smartphone subscriptions worldwide. Second is the dramatic increase in reliance on mobile applications to pay bills and conduct business transactions. Lastly, and not to be overlooked, is the impact that COVID-19 continues to have on cybersecurity. According to a report from Proofpoint, SMiShing increased by over 300% during 2020.
In SMiShing attacks, bad actors may pose as financial institutions, well known retailers, or government agencies. Let’s look at a few examples.
Financial Institutions
Bad actors often use legitimate sounding words and even some branding to help their pretext. Typically, these SMiShing attacks request urgent action to avoid a threat or to resolve a problem. For example, the SMS may say, “your account is suspended,” or it may say, “fraudulent account activity detected.”
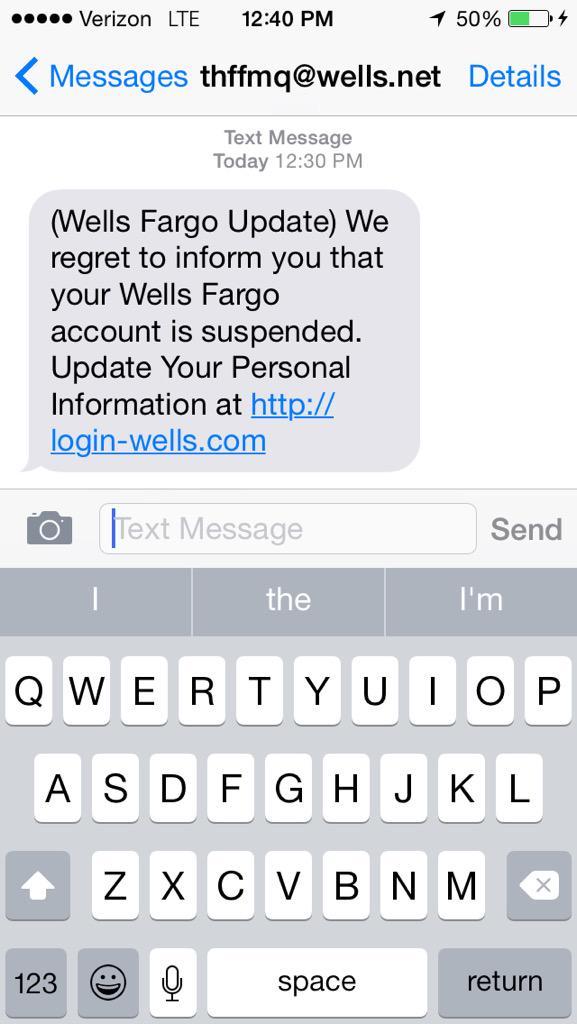
This recent SMiShing scam impersonating Lloyds Bank, a familiar name in England and used by millions of Brits, is making the rounds. One variation of the scam text reads:
“LLOYDS: A new payee has been authorised on 09/02/2021 at 17:55. “If you DO NOT
recognise this, please visit: https://app-payee-cancellation.com/”.
Retail/Trusted Brands
Winning a prize or securing a benefit seem to be the most popular lures criminals use to entice shoppers. For example, this recent Amazon SMiSh says that you’ve won Amazon’s Airpods raffle! All you need to do to claim your prize is click the link to set delivery.
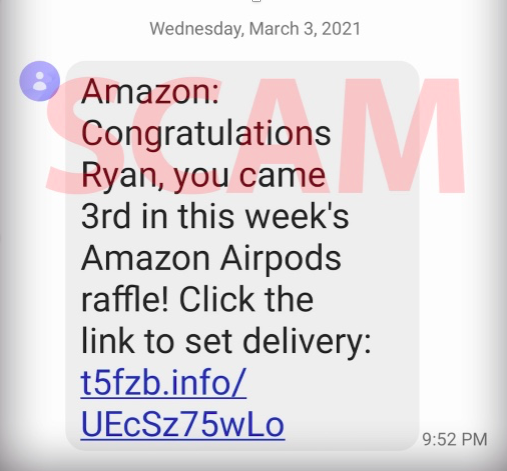
Image: Screen shot of a fake Amazon text (BBB [Better Business Bureau])
Government Agencies
IRS
Criminals commonly impersonate the Internal Revenue Service (IRS). In fact, the IRS now has its own page for reporting phishing, SMiShing, and vishing frauds, as well as tips to avoid fraud.
In December 2020, the IRS and its Security Summit partners issued a warning about a text message scam for the $1,200 Economic Impact Payment. This SMiSH appeals directly to the desire to secure a much-needed benefit. It says in part:
“you have received a direct deposit of $1,200 from COVID-19 TREAS FUND. Further action is required to accept this payment… Continue here to accept this payment …”
Included in the SMiSh is a link to a phishing website. The fake link takes people to a phony website that looks like the IRS.gov Get My Payment website. Once people enter their personal and financial account information, the scammers collect it.
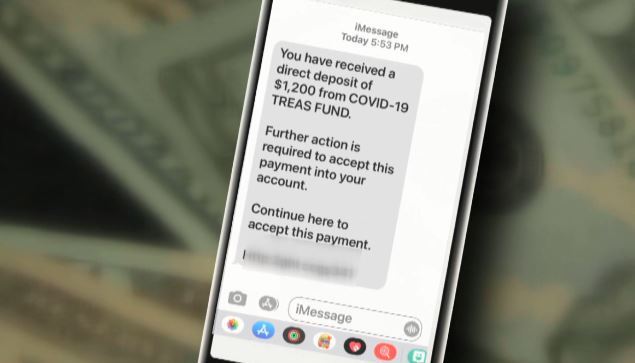
Image: cbs17.com
Department of Health and Human Services
The Department of Health and Human Services (HHS) is another well-known government agency that criminals often impersonate. A recent SMiShing scam going around centers on contact tracing. In this scam, criminals pretend to be contact tracers and send a text message saying that you’ve been in contact with someone who has tested positive for COVID-19. The text message instructs the receiver to click on a link. Clicking on the link will download software onto your device. As a result, scammers now have access to your personal and financial information.
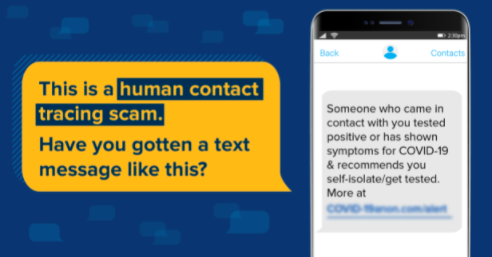 Image: Federal Trade Commission
Image: Federal Trade Commission
Why Adversarial Simulators Use SMiShing in Security Audits
While technical solutions exist to stop SMiShing attacks, there is no practical way to prevent an employee from clicking links, opening attachments, or filling out forms. The best defense is to educate employees and ensure they understand the threats posed by SMiShing attacks. As a result, employees are less likely to click malicious links, and more likely to report suspicious activity. To this end, security awareness training such as, the Managed SMiShing Service, equips leadership to know how their organization will respond to SMiShing attacks.

