IILOVEYOU. Did you ever receive an email with that subject line? Millions did in May 2000. It was a game changer for social engineering and, in fact, saw the beginning of the rise of phishing attacks. Because of the ILOVEYOU virus, social engineering and phishing would, in time, become household words.
When did you first learn about social engineering? For me, it was the year 2012, a whole 12 years after the ILOVEYOU virus attack. I was starting a new job at Social-Engineer, LLC as the Human Hacker’s wrangler (I had no idea what I was getting myself into). To help me understand what the company did, he gave me a copy of his book. I read his book that night and felt like I had entered a new world. Chris’ book gave me a behind-the-scenes look at all the scams and threats that I had heard about but had never seen for myself.
For someone whose childhood existed in a simpler time, this was completely eye-opening to me. Now, in 2020, most have never known any differently. Phishing emails, vishing calls, scams, ransomware…these are now normal. Social engineering and cybersecurity have come a long way since 2000. This month, we’re going back to the past and taking a look at social engineering to see how far it has come.
ILoveYou – 20 Years Ago
On May 5, 2000, the phones of several security professionals all started to ring at once. The calls were from those who were desperately asking for help. They reported a virus that was raging through their systems, destroying and corrupting data as it went. The question of the moment was, “how did this happen?”
The answer was all the same for all of them: one of their employees had received an email with the subject line “ILOVEYOU” and the message, “kindly check the attached LOVELETTER coming from me.” The attachment appeared to be a text file, but it was an executable program masquerading as one. Very quickly the virus took control, sending copies of itself to contacts in the target’s email address book. The recipients, thinking the email was either a joke or a serious declaration of love, opened the attachment. With each click, the virus continued to spread further.
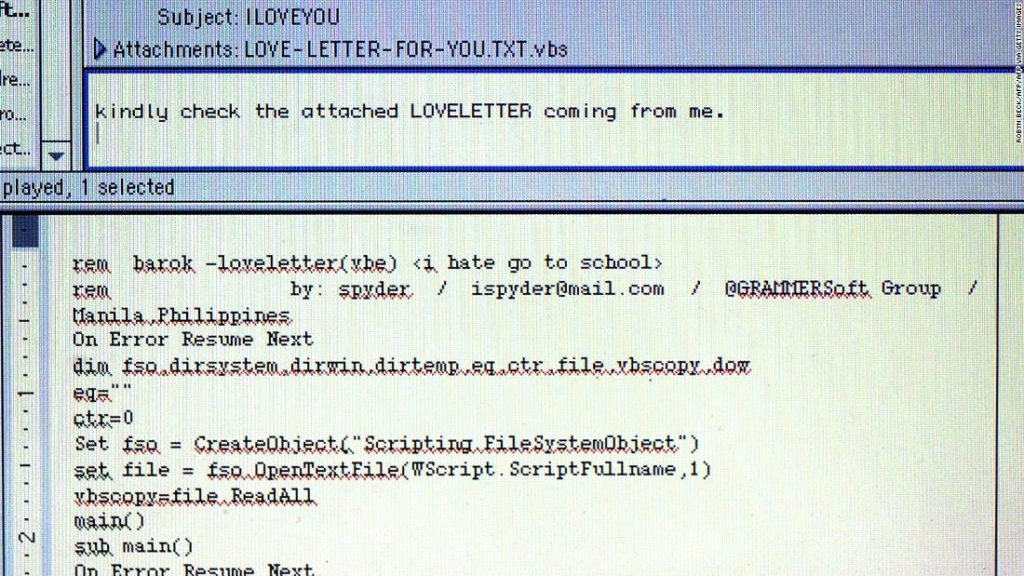
In just five hours, the ILOVEYOU virus spread across Asia, Europe, and North America. Despite warnings being issued, the virus spread through companies like AT&T, Ford Motors, large PR firms, and banks. Government entities like Parliament in Denmark and US Army bases were taken offline due to the spread of the virus. The Pentagon watched as their email services were crippled and forced offline for hours.
Experts began to weigh in on the virus. While the code for the virus was crude, the damage was deep. But, why was this attack so effective? Because it leveraged something that had never been done before.
The Rise of Phishing Attacks
The internet and being online was still a fairly new concept in 2000. Even in the United States, only 43% of Americans were online. In fact, it was only a couple of years earlier, in 1998, that the world was introduced to the idea of online romance via the movie “You’ve Got Mail.” For most people, personal email was still a novel thing. Within the corporate world, businesses were beginning to recognize the usefulness of email and becoming more dependent on it. Email was becoming one of the main ways for professionals to communicate and conduct business. With the increased use of email, scammers quickly started sending unsolicited messages. From there, people learned new words like SPAM. Weeding through junk email became a new daily activity. It was a nuisance, but that email could be dangerous and destructive…that was a brand-new concept for most.
Phishing wasn’t exactly new when the ILOVEYOU virus swept the globe in 2000. In fact, the word “phishing” was added to the dictionary four years prior, in 1996. But most people were still not familiar with the dangers posed by clicking on a link in an unsolicited email. That changed with the ILOVEYOU virus. With the clever use of social engineering, it was now clear that anyone using a computer, whether at home or at work, is vulnerable to attack.
Cybersecurity Had to Change
The ILOVEYOU virus infected over 50 million systems worldwide and cost more than $15 billion to repair. This was a huge blow for corporations everywhere. It grabbed the attention of the entire world and, for the first time, forced it to take cybersecurity seriously.
The ILOVEYOU virus brought attention to two important points. First, antivirus tools and endpoint security are important. Many companies that were infected did not have their data backed up. Second, humans are the weak link. The ILOVEYOU virus spread so quickly because people were willing to open the attachment. The catchy subject line captured their curiosity and they acted on it. Cybersecurity had to change. It was clear now that social engineering attacks could not be ignored, but what could be done? Employees needed education and training to recognize and report social engineering attacks.
Where Are We Now?
That was 20 years ago. So, where are we now? The 2020 Verizon Data Breach Investigations Report (DBIR) presented some interesting statistics. One of the biggest take-aways from that report: people are still the problem. Even though hacking is reportedly down, social engineering accounts for more than two-thirds of attacks. Of those attacks, 96% of them arrive via phishing.
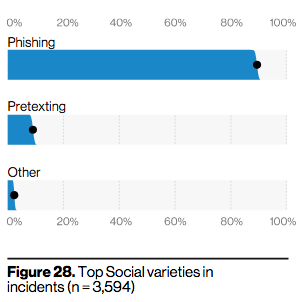
These phishing attacks are often targeting login credentials or personal information. The attacks are often financially motivated. By reaching out to employees who handle the finances or requesting W-2 data from employees, they target the company’s assets. These sophisticated attacks have shown that they are willing to go to any length to achieve success.
The DBIR states that “phishing has been (and still remains) a fruitful method for attackers.” But why, after 20 years, is phishing still so successful? “When an attacker uses the right emotional trigger at the right time, then you have a perfect storm,” says Chris Hadnagy, CEO of Social-Engineer, LLC. Hadnagy has sent over 13 million phishing emails during his career. In his TedX Fulton Street talk, he discusses how chemical releases inside of our brain compels us to say yes or no to things. When the right emotional trigger is hit, and that chemical releases, we are more likely to “say yes.” Or, in the case of a phishing attack, to click.
For Example:
In the present time, we see a plethora of COVID-19 phishing attacks. Hadnagy says the reason these have been so successful is because they hit all the right emotional trigger points. “COVID-19 has created fear, panic, and depression in people. Emails that trigger those 3 emotions will elicit a response without thinking about it first.” In other words, before they can even think about it, they have already clicked. Hearing this leaves many wondering, if phishing attacks are so powerful, how can we ever protect ourselves against them?
The Future is Now
While email clients have gotten better at filtering out malicious-seeming messages, the main weakness that the ILOVEYOU virus exploited remains to be fixed. One expert stated, “You can update your operating systems, or you can have the best email filters in the world, but you can’t patch the human brain.” This means that the future of cybersecurity requires an investment in the human network.
A recent study shows that people now spend 5 hours reading and answering emails each workday. It’s their main channel of communication, and that makes it the riskiest platform in businesses. Therefore, businesses need a new way of thinking to protect their people and the ways that they interact with networks and devices. Securing the human layer requires an approach that understands the human behavior that makes them click. The best defense against these sophisticated attacks is to educate employees and ensure that they understand the value of the information they possess. By addressing security challenges through assessment, awareness, and education, you can help employees understand the threats posed by phishing attacks. Security awareness programs can drastically reduce your target of becoming a victim of phishing.
Security Through Education
Albert Einstein once said, “Education is not the learning of facts, but the training of the mind to think.” We agree. Because of the nature of social engineering attacks, it’s crucial to learn more than just facts—critical thinking is vital. To that end, our mission statement is “Security Through Education.” The Social-Engineer.org framework, newsletters, blogs, and podcasts highlight the value of critical thinking and how it can be applied in day-to-day activities to make a single user or an entire user–base more secure. We invite you to explore our website and learn more about it, as well as the social engineering tactics criminals use to target our emotions. Additionally, our corporate website, Social-Engineer, LLC, offers phishing, vishing, and social engineering risk-assessment training for your organization. Our cutting-edge approach—combining the human network with the digital—provides your organization with the optimal security awareness training.
Aim high. Be an Einstein. Train your mind to think.
Written by: Amanda Marchuck
Sources:
https://www.amazon.com/gp/product/111943338X/ref=as_li_qf_asin_il_tl?ie=UTF8&tag=socialenginee-20&creative=9325&linkCode=as2&creativeASIN=111943338X&linkId=cc1ba9ee7c41ff49ca2f1993dd279a57
https://twitter.com/humanhacker
https://www.social-engineer.com/
https://www.cnn.com/2020/05/01/tech/iloveyou-virus-computer-security-intl-hnk/index.html/
https://www.darkreading.com/threat-intelligence/it-was-20-years-ago-today-remembering-the-iloveyou-virus/d/d-id/1337724/
https://www.cnbc.com/2019/09/22/heres-how-many-hours-american-workers-spend-on-email-each-day.html/
https://www.youtube.com/watch?v=9e6k_PtEXdM

